A trio of transparency scholars have collected personal details of 27,000 intelligence officers they say are working on surveillance programs. The data dump not only names the officers, but in some cases tells you where they live based on data sourced from LinkedIn profiles and other publicly available data sources.
While some will cry foul over this tactic it should be pointed out that this is precisely what these people are doing to law-abiding Americans. Only in much greater detail and using patently illegal methods to do so.
M.C McGrath, founder of Transparency Toolkit, along with coder Brennan Novak and sysadmin Kevin Gallagher have compiled the records into the ICWatch database, which is searchable by company, title, name, and location.
McGrath says the astonishing open-air intelligence reveals details about intelligence officers’ private and work lives. It also reveals troubling previously unknown intelligence programs.
“Luckily it is very easy to find out who is in the surveillance state with just a few Google searches,” McGrath says.
“People post things like ‘I know how to use XKeyScore and MS Word’.”
McGrath was speaking at the Re:Publica conference in Berlin this week, where he identified four spooks using easily-accessible data on LinkedIn, Facebook and other sites to rebuild their personal and work lives.
One blundering spook listed working on more than two dozen surveillance programs including XKeyscore, WealthyCulster, and PinWhale, along with new surveillance programs not currently on the public record.
The revelation of the new programs show that those revealed in the Snowden leaks are just the tip of the iceberg and the full extent of states spying on their citizens is much worse than initially feared.
The research published this week confirm suspicions that every single piece of information shared electronically is logged by the NSA and compiled into dossiers on every single American citizen.
McGrath was able to infer basic definitions of those new codewords based on the context provided on LinkedIn profiles.
“[One officer] identified, collected, and performed direction finding of specific target signals using PENNANTRACE, DISPLAYVIEW and CEGS and it looks like something around geo-location data and airborne SIGINT platforms, so potentially something with SIGINT drones.”
The researchers then probed other online resume sources to learn more about the PENNANTRACE. He found one veteran of some 22 years appeared to have lobbied for “transparency and change” concerning some intelligence programs, swapping jobs within months, before quitting the industry and becoming a used car salesman.
“It’s an indication that people are perhaps trying to change the intelligence community from within,” McGrath says.
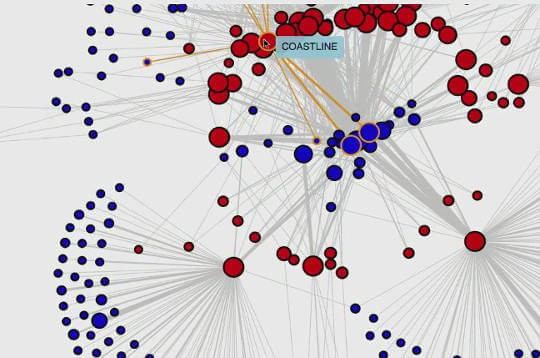
The research team has also created active network graph visualizations showing which companies and LinkedIn members work with which programs, and the relationships between the military and surveillance industries.
That graph data is taken from a LinkedIn feature which shows related profiles.
They also mapped the number of mentions for specific programs over time, which could indicate the commencement of large programs and the agencies involved.
“I’m hoping this data will be used to start debates about programs not previously known …. or to use this information as the basis for FOI (freedom of information) requests”.
McGrath invites interested and capable people to get involved in the project.
The database, named ICSWatch, was down at the time of writing. The cause of the downtime is unknown and highly suspicious.
Stay Connected